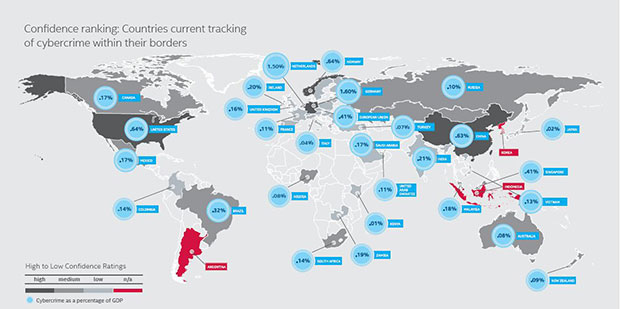
Source: McAfee-CSIS
 Cybercrimes, virtual threats, hacking – all these words dominated headlines last year and earlier this year, with corporations and governments frequently reporting incursions and vulnerabilities in their systems.
Cybercrimes, virtual threats, hacking – all these words dominated headlines last year and earlier this year, with corporations and governments frequently reporting incursions and vulnerabilities in their systems.
In recent years, cybercrimes have caused billions of dollars in losses. Cyber security can no longer be viewed as just a feature for a company or a country – it is an important asset that should be integrated into the whole company or nation’s online ecosystem.
Take for example Sony Corporation’s studio company, Sony Pictures Entertainment’s infamous company-wide cyber attack late last year.
Still recovering from the incident, industry experts observed that the attack could cause Sony about US$100 million as well as a bruised reputation for a perceived failure in safeguarding information from such attacks.
A massive data breach such as Sony’s case can instigate law enforcement investigations, impact revenue, as well as place companies’ competitive information at risk.
More importantly, the cost of cybercrime comes from the damage it causes to the company’s performance and to the national economies.
In a report by Center for Strategic and International Studies (CSIS), sponsored by Intel Security’s cyber security solutions service provider McAfee, titled ‘Net Losses – Estimating the global cost of cybercrime’, CSIS pointed out that cybercrime costs businesses approximately US$400 billion worldwide.
“Cybercrime damages trade, competitiveness, innovation, and global economic growth,” it said.
“For developed countries, cybercrime has serious implications for employment. The effect of cybercrime is to shift employment away from jobs that create the most value. Even small changes in gross domestic product (GDP) can affect employment,” McAfee-CSIS pointed out in the report.
The cyber security landscape will continue to evolve rapidly and attacks will increase in numbers and sophistication, on par with the rapid advancement of technology.
As more corporations and even government agencies leverage on this unavoidable era of connectivity and embrace emerging technologies, new areas of risk exposures are created.
Therefore, it is important to limit this exposure by implementing a multi-level cyber security system into the company or agency and if a cyber attack does occur, experts advise companies or agencies to have a proper post-attack strategy in place to limit its affects on the company or country.
In the case of Malaysia, in 2013, Sophos in its report observed that the country was the sixth most vulnerable towards cybercrimes with RM1 billion losses caused by cyber attacks.
However, industry analysts affirmed that Malaysia has come a long way since then in terms of beefing up its defense strategy against cyber threats.
“The government has shown its commitment and strong focus on ensuring the readiness level across organisations, enterprises and industries, especially those with critical infrastructure such as telecommunication companies (telcos), transportation, banking, defense, government and energy industries,” highlighted Vu Anh Tien, industry analyst of Frost & Sullivan Asia, Pacific Networking, Information & Cyber Security.
“It has proactively introduced multiple regulations and policies, such as the National Cyber Security Policy focusing on the Critical National Information Infrastructure and Malaysian National Crisis Management Plan.
“The government also established dedicated entities like National Security Council, Computer Emergency Response Team, CyberSecurity Malaysia and Malaysian Communications and Multimedia Commission, to assess the readiness and preparedness of critical national infrastructure agencies against cyber attacks.
“These regulations and policies provided great guidance to organisations and enterprises to take action on the cyber threats, helping all critical national information infrastructure entities identify the readiness level against cyber threats,” Vu explained.
He also pointed out that Malaysia’s government has also taken steps in working closely with leading security players to beef up the national cyber security.
“In addition, the long-term visions that the government has lined out recently will help increase awareness toward cyber security, not only government agencies but also private businesses moving forward.”
F-Secure Labs Asia Pacific region security advisor Goh Su Gim commented, “Information and communication technology (ICT) in Malaysia is booming, as there are more penetration of Internet users in the rural areas where access to the Internet via 4G/LTE and inexpensive portable smart devices are enabling users to get online.
“Small and medium sized companies are also jumping on the bandwagon to cloud services such as storage, applications and security.”
However, he viewed, on a cyber security side, users and corporates still lack in terms of awareness and getting basic protection for their devices or companies.
“In our 2014 malware report for Malaysia, 20 per cent of the victims are still infected with primitive age old viruses from seven years ago – which could be prevented through patching of open vulnerabilities in the operating systems.”
Sharing this view, Vu also pointed out that the awareness amongst Malaysian companies towards cyber threats still remains low despite all the efforts that are put into place by the government.
Vu opined, “The key question here is that how can the government turn all these regulations, policies and visions into the factual practices across government agencies and private companies as most of companies in Malaysia remain reactive toward cyber threats due to the low awareness.”
Goh added, “Having an increased cybersecurity awareness level in Malaysia would help the country to fend off cyber criminals, whom are targeting users that are less informed, making a large profit through infected PC’s conducting malicious activities for the hackers (such as sending spam and denial of service or DDOS attacks).
“Once again, Malaysia is a common target for these random hackers as we are considered the ‘lower hanging fruit’ in terms of protection against threats.”
With that, BizHive Weekly takes a look Malaysia’s preparation against cyber threats.
Boosting awareness against cyber attacks
Generally, industry experts believe Malaysian companies are not well prepared against cyber threats due to their lack of awareness of it.
“Companies still view security as a type of cost, but not a business enabler, which caused them to take a restrained attitude towards cyber security investments,” Vu opined.
F-Secure’s Goh further pointed out that in fact, most enterprises today place the responsibilities of IT security on the IT network personnel.
“IT security should be part of the routine, even for all the employees of a company, including awareness and understand the risk and following procedure in not sharing information and password, enforcing the use of strong and frequent passwords change.”
Vu added, from a technology perspective, many Malaysian companies are still taking a reactive approach and lack a holistic defense strategy against cyber security.
“Basic security solutions like network firewall and anti-virus are the most adopted while other advanced technologies like DDoS protection, data and application security, Advanced Persistent Threat protection, and others, are seldom in the purchase list. Furthermore, the lack of advanced threat intelligence solution also causes companies to be passive, and eventually leaves them vulnerable to advanced cyber attacks,” Vu outlined.
And while a company can be well prepared from outside or third-party cyber threats, its own employees can also unknowingly be its Achilles’ heels especially now with the rise mobile devices.
Vu highlighted, the awareness among Malaysian employees toward cyber security still remains low as their understanding of the dynamics in the threat landscape is limited.
“This leaves companies at high risks of being attacked and encountering possible data loss. This is even more dangerous due to the rise of social media and more employees bringing their mobile devices and connecting to corporate networks,” he added.
Similarly, Goh highlighted that malwares are spreading even faster than before, affecting portable devices and Internet of Things.
“As PC sales decline, hackers are turning to infecting and stealing information from these devices, where corporate users are using it for both work and personal use – prompting a nightmare for IT staff to maintain and keeping them secure.
“We have seen mobile malware threats doubling every quarter (especially targeting the Android platform) – and up to 300 new types of Android mobile malware being created every quarter in 2014 – meaning there are three new types of mobile malware created every day!”
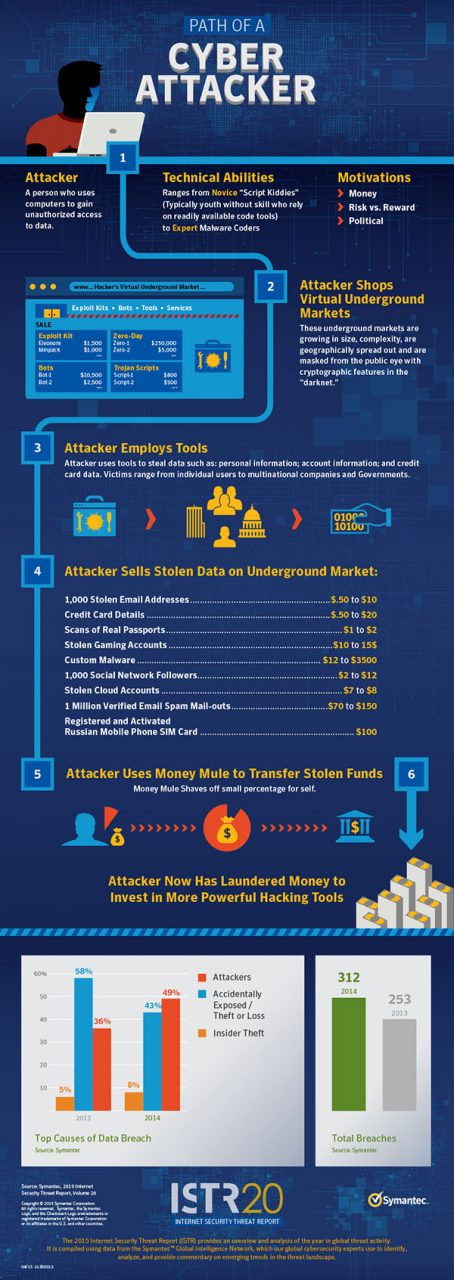
On top of that, according to Symantec Corporation’s (Symantec) ‘Internet security threat report 2015’, in 2014, ‘trojanised’ software updates have made its way online, making it difficult for companies to defend themselves.
“ Attackers identified common software programs used by target organisations, hid their malware inside software updates for those programmes, and then waited patiently for their targets to download and install that software – in effect, leading companies to infect themselves,” it noted.
When it comes to the size of the companies, analysts observe that medium to small enterprises are usually the prime target due to their lower level of cyber security.
Goh pointed out cyber crimes generally target medium to small sized companies as these are the “low hanging fruit” to the hackers and these attacks usually come it the form of exploits targeting unpatched systems that are less maintained in these networks.
Last year, according to Symantec, 60 per cent of all targeted attacks struck small and medium-sized organisations as these organisations often have fewer resources to invest in security, and many are still not adopting basic best practices like blocking executable files and screensaver email attachments.
“It is easier and more profitable by launching attacks in these systems, for example, making the PC’s part of a botnet for the hacker to make money by sending spam through these victims,” Goh said.
He said, while most of these SME’s have either minimal or not IT network staff, they are more focused on getting the infrastructure up and running with minimal downtime, and less time focusing on the security part.
This puts not only the businesses but also their business partners at higher risk.
“It is important for these small enterprises to adopt security as part of their routine, and today, a high level security solution is no longer a highly priced commodity.
“There are many cloud security services where smaller enterprises do not have to invest into expensive equipment (servers and software) for cutting edge protection, thus lowering their capital expenditure.
“With many security offering as a service, they can get protection almost immediately, without the need to maintain resources such as personnel and equipment,” Goh advised.
A strong collaboration is also needed between government agencies and businesses in order to be well prepared against cyber threats.
Vu said these entities need to work together to share threat information and to keep them updated with the technologies.
“The cooperation between the government and enterprises will enable both public and private sectors to enjoy a better security ecosystem to prevent cyber threats.
“We believe that a good preparation should include three dimensions of people, technology and process.
“In terms of people, many companies still lack skilled security professionals that can handle and manage security technologies used in the organisations, and respond to attacks or security breaches,” he commented.
Staying ahead in the virtual protection race
No company, whether large or small, are completely immune from cyber threats or determined, targeted attacks. There is no bullet-proof security system that can guarantee a long-term, completely safe transactions, storage and communication of data on a single network or on a global network.
As threats evolve with technology, its best to constantly be on alert and have a proper cyber security system as well as post-disaster response system, to stand a better chance on limiting losses.
McAfee-CSIS in a report, noted, “For companies, the largest opportunity cost may be in the money spent to secure their networks.
“While companies would always spend on security even if risk in the digital environment was greatly reduced, there is a ‘risk premium’ that they pay for using an inherently insecure network.”
Aside from a continuous protection against cyber attacks, companies should also have an appropriate response strategy in place.
“Cleaning up in the aftermath of cyber crime is expensive, often more expensive than the crime itself,” McAfee-CSIS pointed out.
It observed, the clean-up cost could increase ten-folds compared with the actual losses directly attributed to hackers and the recovery companies must implement in the aftermath of those attacks.
“In order to be well prepared against cyber threats, companies need to have a comprehensive plan to strengthen their security systems, policy enforcement as well as post-incident response strategy,” Vu stressed.
“First of all, security budget needs to be at the top of the list. The sufficient budget allocation will allow companies to purchase new security solutions and technologies to strengthen their infrastructure.
“The budget is also used to help organisations in training or hiring staff, or engage with a third party service provider to do the job,” he explained.
Risk assessment is also critical in the preparation and prediction of possible forthcoming cyber attacks.
Vu noted that risk assessment should be done often so companies can have a clear picture of their security posture as well as the risk the company might face in the future.
“In this light, companies can work with an managed security service provider (MSSP) to provide penetration and vulnerability testing as well as security consulting services before taking action to put necessary technologies and best practices in place,” he suggested.
Aside from that, Vu noted, when putting technologies in place, it is important for organisations to take a holistic approach toward security deployment to increase the overall protection efficiency.
“A comprehensive defense strategy that covers all form factors, including network, end-point, content in both physical and cloud environments will greatly help maximise protection level of the security system.
“More importantly, companies need to be more proactive to cyber security, meaning that they must be kept updated on the dynamics of threat landscape as well as latest security technologies to prevent these threats, especially those threats exploiting zero-day vulnerabilities.
“Not only the IT department should do this, other business departments of the organizations also need to be kept involved in the process.
“As a result, a regular basic security training course for all staff would be critical for the company to stay ahead of cyber threats,” he explained.
Beyond the companies themselves, it is also important for government agencies and enterprises to work together to form a united front and to strengthen the whole ecosystem across public and private sectors against cyber attacks.
Goh also noted, there is still a lot of awareness and education required in terms of cyber security.
“Having an increased cybersecurity awareness level in Malaysia would help the country to fend off cybercriminals, whom are targeting users that are less informed, making a large profit through infected PC’s conducting malicious activities for the hackers (such as sending spam and DDOS attacks),” he added.
Goh also suggested, more programmes could be run on a national level, such as incorporating training and education in schools, even the young ones such as primary school as today’s children are more expose to online social media and technically savvy.
“Users in Malaysia today should also know how to respond in case they are breached and hacked. It is important to report incidents to the authorities so that they can assist in taking the right action against malicious activities,” the cyber specialist added.
All in, Frost & Sulivan’s Vu pointed out that companies of all sizes need to understand the threat landscape, risks and the importance of security technologies and its impacts to their daily business.
“In the highly competitive landscape, security has become an enabler for companies to increase business operations, Malaysian companies also need to understand that security is not an IT problem, but a business issue, and it should be viewed as investment, not a cost.
“In many ways, security needs to be tied to business decision, a part of every single business process, and duty of all departments and staff.”
Cyber threats predictions for 2015: Attack on devices
In 2015, industry experts expect to see another stage in the evolution of cyber criminal with the increase of adoption of advanced package tool tactics and finance-motivated attacks.
In particular, analysts generally view that as consumers grow increasingly connected to the online world especially with the increase of smart devices and wearable technology, they view that attacks on Internet of Things (IoT) will increase rapidly.
“It’s a fast-moving environment where innovation trumps privacy. Short of government regulation, a media-friendly scare story, or greater consumer awareness of the dangers, it is unlikely that security and privacy will get the attention they deserve.
“The market for Internet of Things–ready devices is growing but is still very fragmented, with a rich diversity in low-cost hardware platforms and operating systems.
“As market leaders emerge and certain ecosystems grow, the attacks against these devices will undoubtedly escalate, as has already happened with attacks against the Android platform in the mobile arena in recent years,” Symantec said in a report.
McAfee, meanwhile, viewed, IoT devices will face more aggressive attacks due to the hypergrowth in the number of connected objects, poor security hygiene, and high value of data on IoT devices.
On the other hand, Trend Micro in a report, observed that while attacks are bound to happen to IoT devices, it believed that aided by the formation of Open Interconnect Consortium (IOC) and the launch of HomeKit, common protocols and platforms should slowly emerge.
However, it warned, “As attackers begin to better understand the IoE/IoT ecosystem, they will employ scarier tactics akin to ransomware and scareware to extort money from or blackmail device users.”
For now, it noted, due to the lack of a “killer app” as well as the diversity of IoT devices, cyber attackers will not likely launch a financially-motivated attack of IoT users.
Aside from that, other top predictions for 2015 include increased attacks or attempts to attack financial institutions and online payment systems.
Kaspersky in its 2015 prediction report, noted that as some countries adopt virtual payment systems, it expected cyber criminals to leap at the opportunity to exploit this.
“Whether social engineering the users, attacking the endpoints (cellphones in many cases) or hacking the banks directly, cyber criminals will jump all over directly monetised attacks and virtual payment systems will end up bearing the brunt.
“These fears can also be extended to the new Apple Pay, which uses near field communications (NFC) to handle wireless consumer transactions,” it said.
Trend Micro it its 2015 Security Predictions report, said that in the next few years, cyber criminals will no longer just launch financially motivated threats against computer users but mobile device users as well.
“They are likely to use fake apps and domain name system (DNS) changers and launch mobile phishing attacks similar to those we’ve already seen in the past,” it explained.
“The growing risks online banking threats pose should motivate individuals and organisations alike to use the two-factor authentication meassures and hardware or session tokens that banks and other financial institutions provide,” Trend Micro observed.
Meanwhile, Symantec viewed that the future of cyber security could lie in a unified security system.
“Advanced attackers use exploit toolkits against not only older vulnerabilities but also new, zero-day ones, and being good at defense means being harder to breach.
“The battle is an asymmetric one, and attackers already understand the defenses and their weaknesses. A unified security model is not just about investing in great technology. It also takes a holistic approach that combines threat intelligence, risk management, and the very best technical solutions.
“A unified approach will not only help reveal who is being targeted but also how and why.
“Understanding the new threats is critical, and businesses should now expect to be attacked—the question is not ‘if’ but ‘when’ and ‘how’.
“Unified security can leverage the combined visibility and threat intelligence gathered across the enterprise to block, detect, and remediate attacks.
“It can help guide how to better protect confidential information and reduce risk, supporting the continual assessment of not only people and their skills but also processes and technology to ensure the best response is followed.
“Processes are continually updated and skills maintained. Ultimately, by becoming harder to breach, attackers must work harder; no one wants to be the weakest link in the supply chain. This, we believe, is the future of security,” it explained.
